Share this
Making a Business Case for Information Security Training
by Reflare Research Team on Mar 17, 2023 6:49:00 PM
While information security training is an absolute necessity for any modern organisation, it can be surprisingly difficult to convince decision-makers to allocate funding, let alone perform a successful rollout.
First Published 9th December 2020 | Latest Refresh 17th March 2023

"Throw your hands up in the air and wave them if you keep your password on a post-it note!"
8 min read | Reflare Research Team
The Main Process Steps
In this article, we will guide you through the essential steps required to get IT security training for both tech and non-tech staff approved, funded and implemented.
Before diving into the details, let’s get the main process steps out of the way first. These are the pillars that your business case is built upon. While their specifics will vary depending on your organisation, they always need to be rock-solid as they underpin everything else you do.
1. Document Your Business Case
Gather all of the intelligence related to information security training in your organisation in one place. Examples of data you will want to gather include, but are not limited to:
- How many staff members need to be trained?
- By when and at what recurring intervals does the training need to take place?
- Are you subject to legal, contractual, or policy-based guidelines on what needs to be trained?
- Is your workforce uniform or does it consist of separate groups (e.g. “IT” and “sales”)?
Having all of this information in place, organised, and appropriately tagged will allow you to both convince decision-makers of the requirement for funding and roll out a training program with minimal friction.
If you feel like you lack the capability to accumulate this information, this is the right point in time to add experts to your team.
2. Get Decision Maker Approval
Gather all of the intelligence related to information security training in your organisation in one place.
If your decision-maker is a CISO or if you are the decision-maker, this will be the easiest part. Otherwise, it might be the hardest. Find out who the decision-maker is and tune your proposal to them. An IT manager will need different information than an on-technical board.
The information gathered in step 1 will be used as the basis for this step. Highlight the benefits of training your workforce. Points to highlight include:
- The cost of training vs. the cost of a breach
- Explaining that turnkey solutions such as web application firewalls and endpoint protection can are not replacements for a well-trained workforce
- Training currently in place with competitors
- Legal, contractual, or policy-based training requirements you might be under
3. Track the Ongoing Execution of Your Training
Once funding is approved and training is rolled out, it is essential that you establish a tracking routine. While all reputable information security training solutions come with tracking and analytics built-in, you will need to establish reporting schedules and metrics.
Questions to ask include but are not limited to:
- Who needs to take the training?
- When will they finish the training?
- At what intervals will users be automatically notified about upcoming or passed deadlines?
- What are the processes and penalties in place for training failure?
- At what intervals is the training solution itself evaluated?
How Does Information Security Training Improve Security?
This is the core question you need to answer in your proposal. If training does not improve security, then it is a waste of resources. In the following paragraphs, we will walk you through the general benefits of good training solutions. You will need to adapt and adjust them to the on-the-ground reality of your organisation.
Identifying Risks and Challenges
The process of implementing and executing information security training forces an organisation to evaluate and understand the risks it faces related to its infrastructure. If done correctly, it also leads to an inventory of systems, data, assets, staff roles, staff capabilities, and risk surfaces.
If insufficiencies exist within the organisation, the process of training will likely make them become apparent. This in turn is the first step toward mitigation.
Protect Assets and Infrastructure
The better trained your workforce is, the less likely a breach becomes and the smaller the impact of a breach will be. Apart from direct financial losses due to theft, downtime, and destruction, organisations increasingly also experience losses caused by ransomware, government fines, loss of consumer trust, and theft of intellectual property. Since the losses caused by successful breaches are often massive, money invested into training tends to have a very high return on investment.
It is important to note that as a rule of thumb, the weakest organisation in a given vertical is most likely to be hacked. Attacks cost money and attackers will usually go for the lowest hanging fruit. By training your workforce, you increase the resilience of your organisation which in turn increases the cost of hacking it. With a higher cost, the next cyber-attack might hit your competitor instead of yourself.
Detect Breaches Faster
Even with the best security policies and systems in place, breaches do happen. One of the factors with the biggest impact on how costly a breach is for the organisation is the time to discovery. Breaches that are discovered, stopped and mitigated in minutes cause repercussions that are orders of magnitude smaller than those that go unnoticed for years.
Training your workforce reduces time to detection in multiple ways. For one, the formalization of assets and staff roles leaves less ambiguity for attackers to work with. With clear rules established and your workforce trained on them, attackers are much less likely to be able to trick your staff or exploit forgotten systems. For another, better-trained IT staff makes fewer mistakes, which in turn reduces the attack surface of your infrastructure.
Lastly, staff members tend to default to inaction. If something suspicious is detected but no clear rules for reporting or guidelines for normalcy are in place, then no report will be filed. And without reports, detection will take a long time.
Respond to Breaches Faster
Once breaches are detected, they need to be mitigated. This requires both specialists and cooperation from your wider workforce. Specialists rely on regular employees to inform them about abnormalities they experience. And abnormalities can only be detected in contrast to an established rule.
Unless you train your staff members on what to expect, any irregularities resulting from a breach could simply be changes made to the system.
Recover From Breaches Faster
Lastly, good training will make a recovery from breaches much faster and less costly. For one, the combination of quicker detection and response will limit the damage that is done to your organisation. For another, better-trained staff and more clearly defined resources make it easier to repair the damage that has been caused.
Identifying Benefits
Based on the points outlined in the previous section, you now need to establish key benefits for the proposed training implementation. To do so, you require access to key metrics. These metrics will vary widely based on the size and kind of your organisation. Examples include but are not limited to:
- Number of breaches per year
- Average time to detection per breach
- Total monetary damage through cyber attackers per year
- Average time to full recovery per breach
- Percentage of staff members failing phishing drills
- Number of security vulnerabilities identified during pre-release audits
If you do not have access to the metrics you need, this is the time to gain access. Find the people that hold the information and build pipelines for the information to regularly make its way to you.
It is also likely that some of the metrics do not yet exist. If they can be derived from existing metrics, put a system in place to do so. If not, include the creation of set metrics in your proposal. In any organisation, projects live and die by numbers. Make sure that you have access to the numbers you need.
Once the metrics are in place, codify them into benefits for reporting.
If adjacent companies publish their own metrics, this is a great time to borrow their figures to estimate the impact training will have on your organisation. Make sure not to forget to scale all figures relative to organisation size and risk surface.
Also, resist the trap of using easy metrics that do not apply to your needs. For example, if your organisation is 98% non-IT, then the results of pre-release audits may be very easy to get and clean-cut but they are also almost meaningless for your general security.
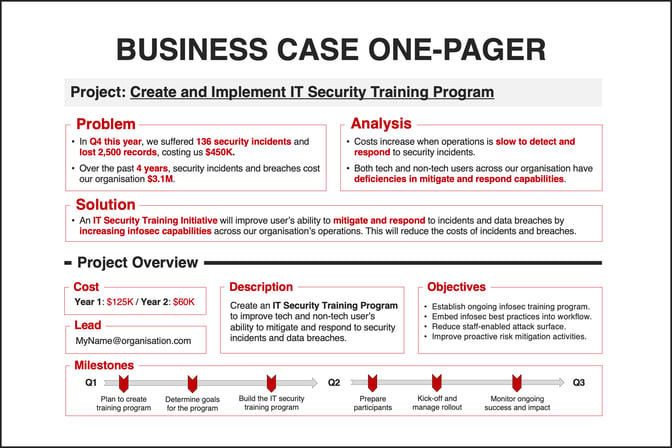
Download: This is a useful "tear-out" for both tech and non-tech leaders to consume your case from problem to analysis to solution in a digestible format. (pdf) / (ppt)
Establish Risks and Mitigations
The risks associated with information security training fall into three major categories:
1) The Budget For Your Training Outweighs the Benefits
This can happen if your chosen training is a bad fit for your organisation or if the training is of low quality in general.
To mitigate this risk, perform a thorough evaluation of available training options and fit them to the requirements established in previous sections.
Resist the urge to buy from the best-known vendor in your field since those vendors are often generalists that cannot provide the best solution for your particular targets.
2) Performance Metrics Are Not Met
This point strongly correlates to (1). Unmet performance metrics are either caused by a bad fit, a misunderstanding of your organisation’s needs, or bad employee compliance.
Mitigating this problem requires you to first understand which of these three factors (or which combination) is the root cause. Bad training fit can be mitigated by different training. False assumptions about your organisation’s requirements can be mitigated by a renewed audit of your goals and assets. Insufficient compliance can be mitigated through improved incentive and punishment structures.
3) The Training Fizzles Out and is Never Fully Implemented
Hopefully following this guide will prevent such a scenario but it is important to remember that projects without clear goals, reporting guidelines and staff assignments can end up in limbo when key decision-makers are replaced.
Ensure that you either control the execution and budget of the training rollout or that guidelines are in place should the person who does be replaced.
The benefits you identify in the previous section will also allow you to see if the training you implemented is adequate. If after a while the metrics do not show improvement relevant to your organisation, it might be time to look for a new vendor with a better fit.
Understanding every possible scenario that you need to train for will ultimately be impossible. However, keeping up to date with the challenges other organisations are currently facing will save you time, effort, and pain! Review some of our related research briefs, and learn from the misfortune of others.
Share this
- February 2026 (1)
- January 2026 (1)
- December 2025 (1)
- November 2025 (1)
- October 2025 (1)
- September 2025 (1)
- August 2025 (1)
- July 2025 (1)
- June 2025 (1)
- May 2025 (1)
- April 2025 (1)
- March 2025 (1)
- February 2025 (1)
- January 2025 (1)
- December 2024 (1)
- November 2024 (1)
- October 2024 (1)
- September 2024 (1)
- August 2024 (1)
- July 2024 (1)
- June 2024 (1)
- April 2024 (2)
- February 2024 (1)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (1)
- September 2023 (1)
- August 2023 (1)
- July 2023 (1)
- June 2023 (2)
- May 2023 (2)
- April 2023 (3)
- March 2023 (4)
- February 2023 (3)
- January 2023 (5)
- December 2022 (1)
- November 2022 (2)
- October 2022 (1)
- September 2022 (11)
- August 2022 (5)
- July 2022 (1)
- May 2022 (3)
- April 2022 (1)
- February 2022 (4)
- January 2022 (3)
- December 2021 (2)
- November 2021 (3)
- October 2021 (2)
- September 2021 (1)
- August 2021 (1)
- June 2021 (1)
- May 2021 (14)
- February 2021 (1)
- October 2020 (1)
- September 2020 (1)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2020 (2)
- March 2020 (1)
- February 2020 (1)
- January 2020 (3)
- December 2019 (1)
- November 2019 (2)
- October 2019 (3)
- September 2019 (5)
- August 2019 (2)
- July 2019 (3)
- June 2019 (3)
- May 2019 (2)
- April 2019 (3)
- March 2019 (2)
- February 2019 (3)
- January 2019 (1)
- December 2018 (3)
- November 2018 (5)
- October 2018 (4)
- September 2018 (3)
- August 2018 (3)
- July 2018 (4)
- June 2018 (4)
- May 2018 (2)
- April 2018 (4)
- March 2018 (5)
- February 2018 (3)
- January 2018 (3)
- December 2017 (2)
- November 2017 (4)
- October 2017 (3)
- September 2017 (5)
- August 2017 (3)
- July 2017 (3)
- June 2017 (4)
- May 2017 (4)
- April 2017 (2)
- March 2017 (4)
- February 2017 (2)
- January 2017 (1)
- December 2016 (1)
- November 2016 (4)
- October 2016 (2)
- September 2016 (4)
- August 2016 (5)
- July 2016 (3)
- June 2016 (5)
- May 2016 (3)
- April 2016 (4)
- March 2016 (5)
- February 2016 (4)


