The Fifth Third Bank Breach - Banks and Insider Threats
by Reflare Research Team on Sep 13, 2022 6:24:00 PM
We’re starting to see a pattern emerge in the reporting that financial institutions use when they’re breached. Fifth Third Bank, one of the top 20 banks in the US, is yet another high-profile organisation to have suffered a major security incident. First Published 25th February 2020 | …
Stop 3rd Party Security Vendor Backdoor Leaks Before They Bite
by Reflare Research Team on Sep 13, 2022 6:18:00 PM
Several major networking equipment providers were found to have backdoors in their firmware that exposed private keys and even allowed remote code execution. If you’re not yet worried, then you’re not paying attention.
The Black Market for Accounts
by Reflare Research Team on Sep 13, 2022 6:13:00 PM
While black markets have existed since the early days of the internet, recent technological changes have made them a much more lucrative and popular option than before. The value of credentials for services like Disney+, Netflix and AWS will continue trending upward as long as there’s …
InterContinental Hotels Group Card Data Hack
by Reflare Research Team on Sep 13, 2022 5:47:00 PM
If reports were correct, this was one of the hospitality industry's largest data breaches to date. With nearly 1,200 hotels affected, the breach was large enough to reach out and touch a significant portion of the 61 million IHG stays per year. First Published 20th April 2017 | Latest …
Cybercrime in an Interconnected World
by Reflare Research Team on Sep 13, 2022 1:01:00 PM
Cybercriminals are not confined to one region or culture, but operate throughout the interconnected world to capitalise on evolving opportunities to steal customer data and transfer funds. Published 25th May 2016 | Latest Refresh 13th September 2022 A web that reaches from a pocket in …
Proof of Attack vs Proof of Attacker
by Reflare Research Team on Sep 13, 2022 12:46:00 PM
When a system is said to be under attack, compromised or a breach is suspected and/or detected, given the physical and technical challenges, is it even possible to prove who did it? First Published 15th December 2016 | Latest Refresh 13th September 2022 Sufficient due process to separ …
The FriendFinder Hack and the Value of Customer Data
by Reflare Research Team on Sep 13, 2022 12:36:00 PM
FriendFinder was the victim of a cyber attack leading to a data leak, including usernames and passwords for 412 million accounts. The hack is one thing, but the blackmail! Oh, the blackmail. First Published 16th November 2016 | Latest Refresh 13th September 2022 Stephen, 31, persists …
The Accessible Guide to Penetration Testing
by Reflare Research Team on Sep 7, 2022 7:43:00 PM
For years, penetration testing was viewed primarily as an activity for large and complex companies. Now that it is significantly more accessible, smart (and less sophisticated) businesses are baking it into their business-as-usual activities even as early as the point of their creatio …
Cybersecurity Recruitment, Education, and Neurodiversity
by Reflare Research Team on Sep 1, 2022 7:40:00 PM
Companies are screaming for new cybersecurity professionals to join their teams. However, they are going out of the way to make their recruitment as difficult as possible.
The Blind(ish) Eye of Local Government Cybersecurity
by Reflare Research Team on Sep 1, 2022 7:27:00 PM
The level of understanding many state and local agencies possess about their cybersecurity capabilities is disturbing. We asked why they knew so little, and the answers we received made us cringe with despair. First Published 31st January 2022 | Latest Refresh 1st September 2022 "Ever …
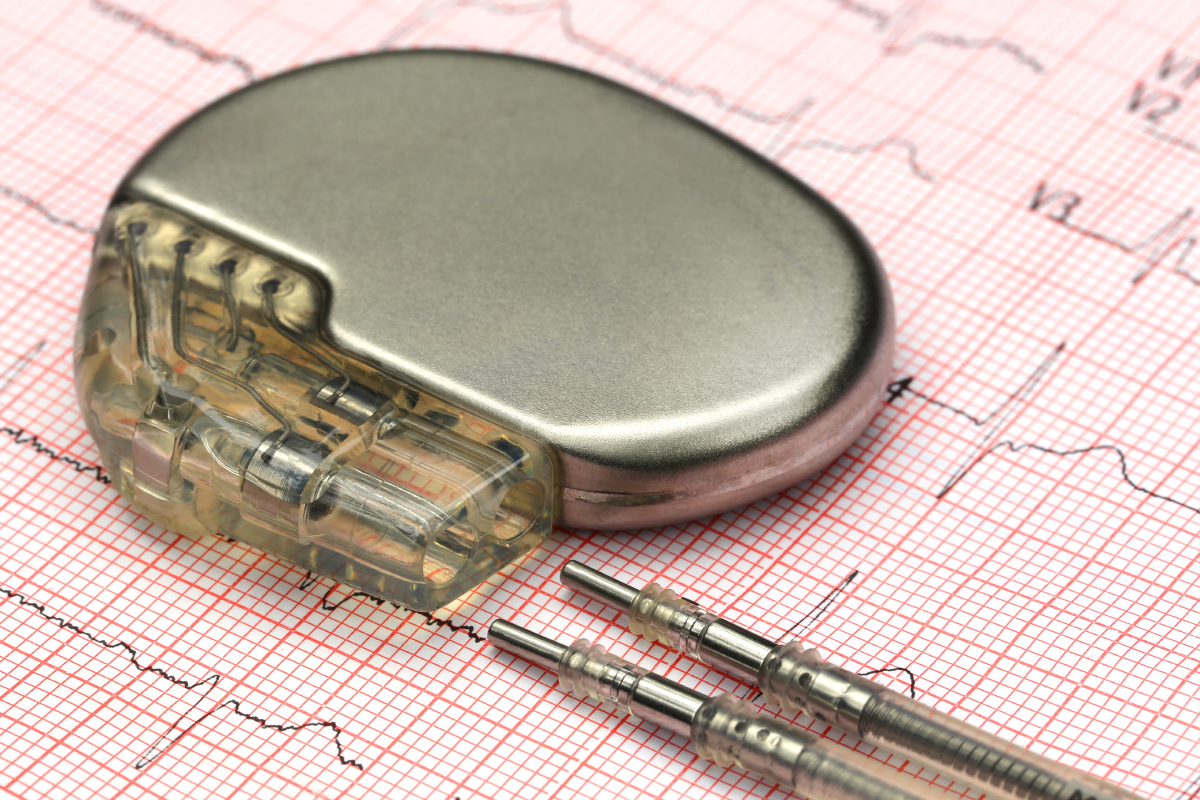
Hackable Medical Implants and Somebody Else's Fault
by Reflare Research Team on Sep 1, 2022 3:12:00 PM
Those of you into (anti)lifehacking might have already heard about the exploitable risks with implantable cardiac devices. This is no longer a "once in a blue moon" kind of attack, but something that the medical implant industry really needs to get on top of. First Published 10th Augu …












%20Eye%20of%20Local%20Government%20Cybersecurity.jpg)