The FriendFinder Hack and the Value of Customer Data
by Reflare Research Team on Sep 13, 2022 12:36:00 PM
FriendFinder was the victim of a cyber attack leading to a data leak, including usernames and passwords for 412 million accounts. The hack is one thing, but the blackmail! Oh, the blackmail. First Published 16th November 2016 | Latest Refresh 13th September 2022 Stephen, 31, persists …
The Accessible Guide to Penetration Testing
by Reflare Research Team on Sep 7, 2022 7:43:00 PM
For years, penetration testing was viewed primarily as an activity for large and complex companies. Now that it is significantly more accessible, smart (and less sophisticated) businesses are baking it into their business-as-usual activities even as early as the point of their creatio …
Cybersecurity Recruitment, Education, and Neurodiversity
by Reflare Research Team on Sep 1, 2022 7:40:00 PM
Companies are screaming for new cybersecurity professionals to join their teams. However, they are going out of the way to make their recruitment as difficult as possible.
The Blind(ish) Eye of Local Government Cybersecurity
by Reflare Research Team on Sep 1, 2022 7:27:00 PM
The level of understanding many state and local agencies possess about their cybersecurity capabilities is disturbing. We asked why they knew so little, and the answers we received made us cringe with despair. First Published 31st January 2022 | Latest Refresh 1st September 2022 "Ever …
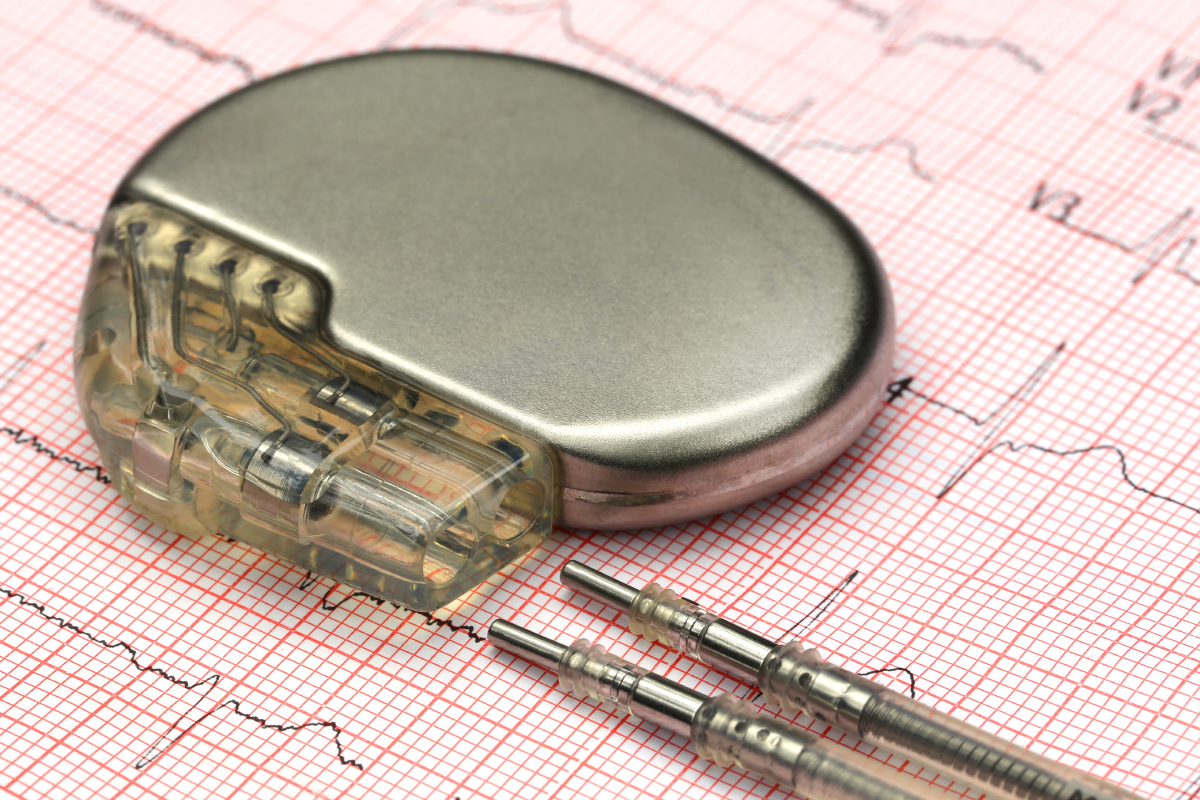
Hackable Medical Implants and Somebody Else's Fault
by Reflare Research Team on Sep 1, 2022 3:12:00 PM
Those of you into (anti)lifehacking might have already heard about the exploitable risks with implantable cardiac devices. This is no longer a "once in a blue moon" kind of attack, but something that the medical implant industry really needs to get on top of. First Published 10th Augu …
The Weakness of Academic Cybersecurity
by Reflare Research Team on Aug 18, 2022 5:21:00 PM
A penetration test conducted for a UK government agency came out with one simple conclusion - 100% of UK universities and academic institutions have shockingly weak cyber security. Just ask the University of Sunderland. First Published 8th April 2019 | Latest Refresh 18th August 2022 …
Selecting the Right Cybersecurity Training Solution
by Reflare Research Team on Aug 15, 2022 7:01:00 PM
Learning and development teams are increasingly outsourcing the creation and delivery of IT security training to other departments or third-party vendors. However, not being aware of the limitations of your training solution may be worse than not training at all.
The Rise of Cybersecurity as a Political Hammer
by Reflare Research Team on Aug 9, 2022 6:58:00 PM
To this day, governments have many reasons to try limiting the use of strong cryptography. However, when did this trend move into the mainstream consciousness and become an issue directly engaging wider society? Prior to the 2016 U.S. election cycle, a controversial bill was tabled wi …
Hey Biotech - These New Problems Are Not What You Think
by Reflare Research Team on Aug 7, 2022 7:22:00 PM
Biotechnology companies are starting to look more and more attractive to hackers, and a number of successful exploits should give pause to industry leaders. However, things are not quite what they seem. First Published 14th January 2022 | Latest Refresh 7th August 2022 "Nope! Can't fi …
The Future of Passwords
by Reflare Research Team on Aug 5, 2022 7:17:00 PM
Companies are entirely aware of the challenges posed by passwords as an authentication mechanism, and continue to find a way to replace them with something better. But are they good enough? And more importantly, are users ready to change?






%20Eye%20of%20Local%20Government%20Cybersecurity.jpg)